Risk management
Applications for risk management
They provide significant assistance in ensuring compliance between internal risk management policy and external requirements. Due to their simplicity and the way they work with risk, the applications significantly save the time and resources needed for effective dynamic risk management.
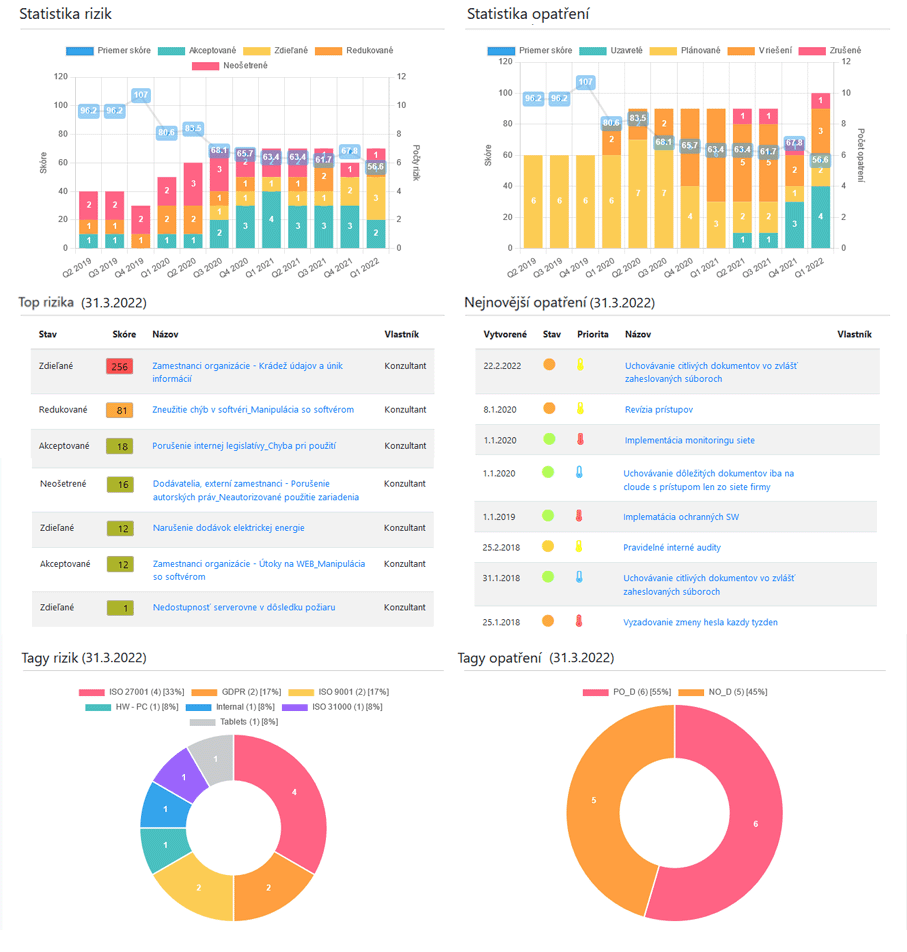
Q-integra Risk as default application is used to manage information and operational risks throughout their entire lifecycle – from identification through analysis, assessment, treatment and monitoring.
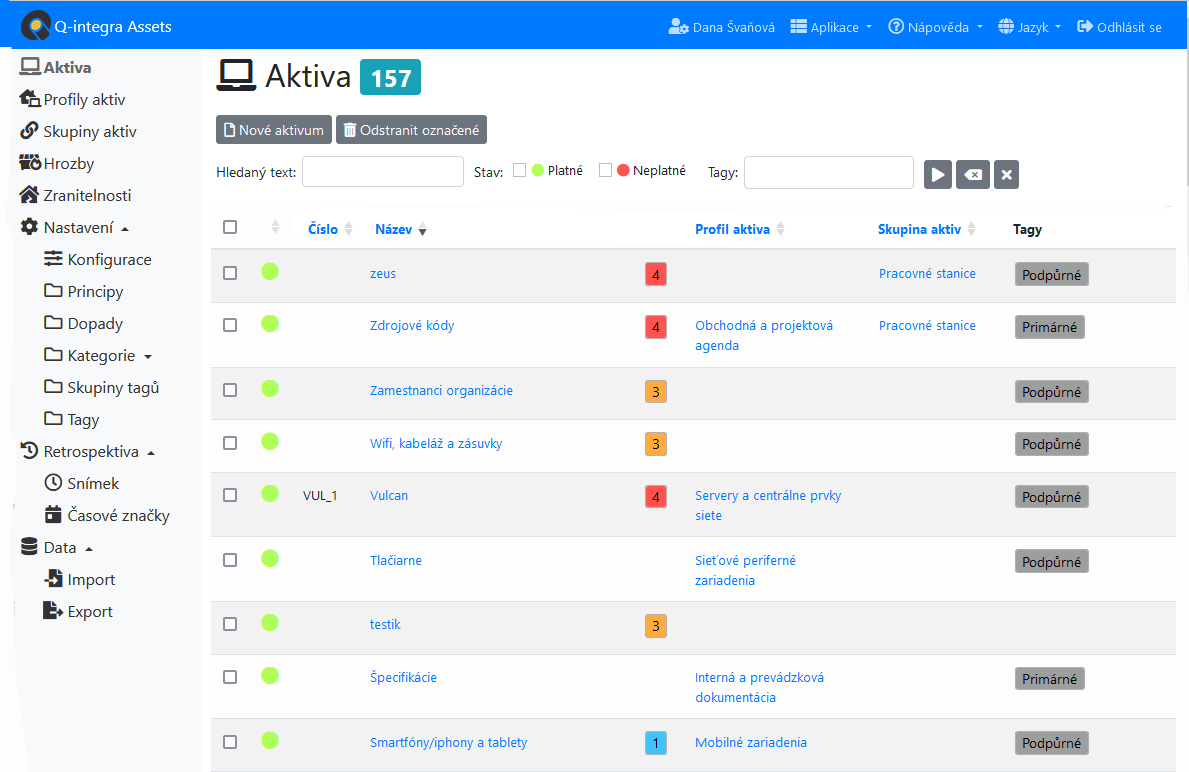
The Q-integra Assets add-on module allows the creation of a comprehensive asset catalogue with the ability to categorise assets and groups for bulk assignment of threats and vulnerabilities.
The Q-integra Requirements Register application is a tool for evidencing and assessing legal, statutory, regulatory, contractual and other requirements that apply to an organisation.

Q-Risk – effective tool for risk management
- identification of risks with the possibility of linking them to assets,
- risk categorisation,
- implementation of own risk assessment methodology,
- easy input of assessment parameters,
- risk treatment management,
- risk monitoring,
- copying of reference risks and measures,
- treatment of identified threats and vulnerabilities to the organisation’s assets (Risk Matrix),
- support for multiple risk management domains,
- migration of data from other systems.
Q-Assets – additional module for information risk management
- a platform for identifying information risks,
- recording, assessment and categorisation of assets with a link to their threats and vulnerabilities,
- pre-prepared catalogues of generic threats and vulnerabilities,
- impact analysis (BIA) with user parameterisation and asset value calculation,
- threat and vulnerability management in asset profiles,
- data import and export.
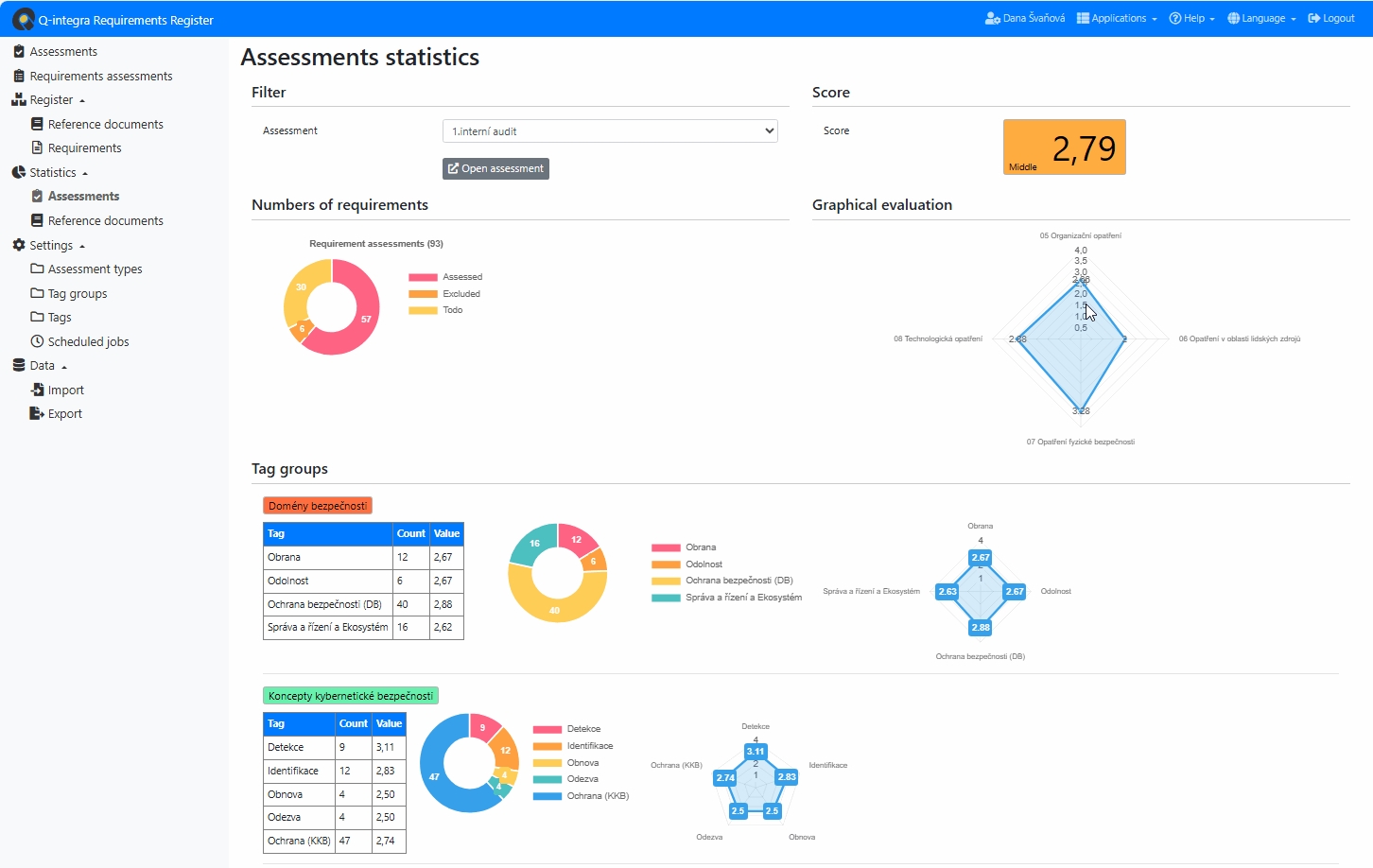
Q-Requirements Register – evidencing and assessing requirements
- evidencing legal, statutory, regulatory, contractual and other requirements for the organisation,
- assessing compliance with the requirements in the form of their evaluation,
- linking requirements to the organisation’s actions and risks,
- statistical outputs and generation of XLS file with assessment data,
- custom settings of the assessment system and requirement categories,
- export and import of requirements and assessments.